Summary
In this article we will learn about the process involved in Creating k8s Cluster and adding Linux/Windows Node
Prerequisite
Linux Physical or virtual machine for Master and Linux/Windows physical or virtual machine as Nodes (Minions)
Bootstrapping a Cluster with kubeadm
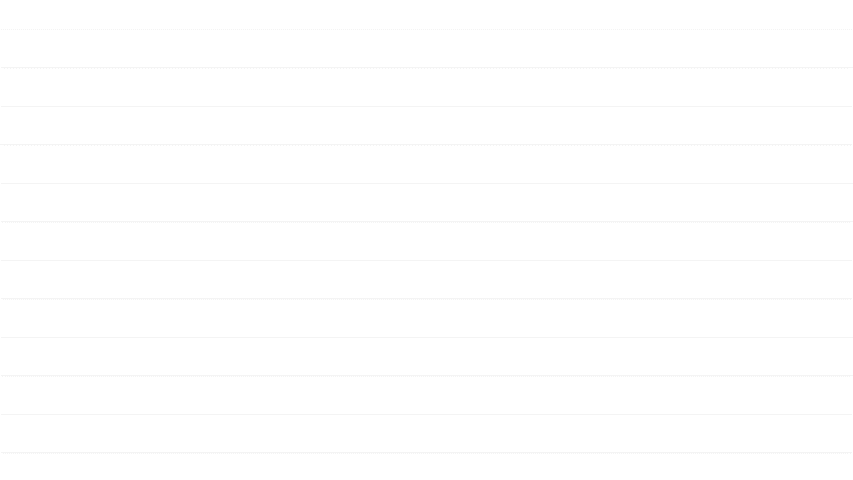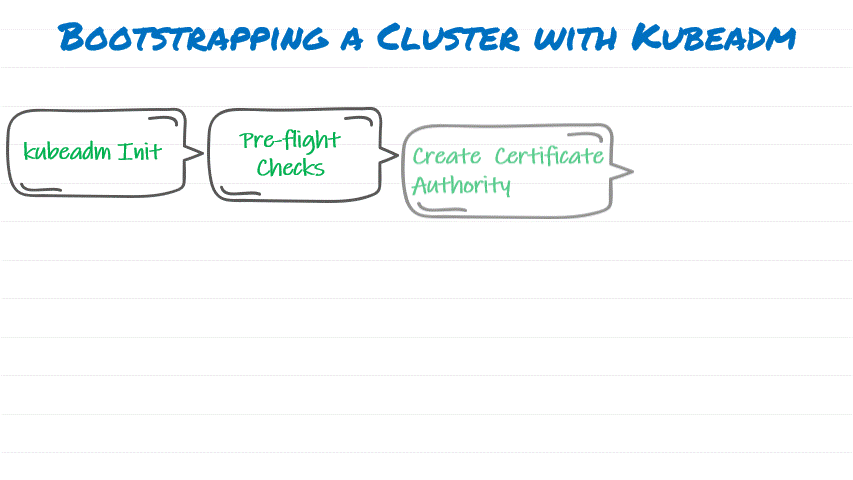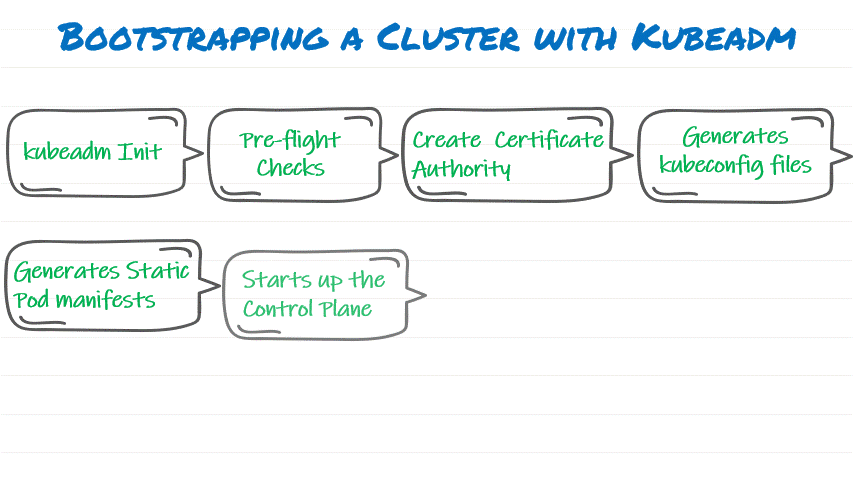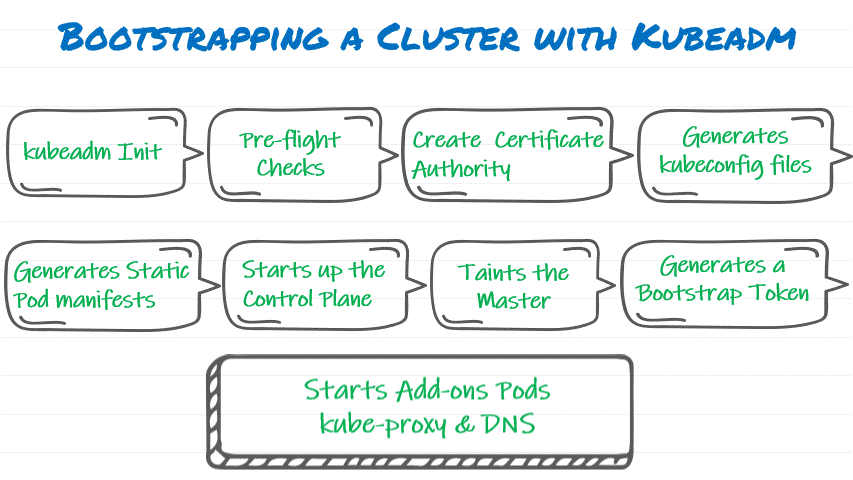
Step by Step process:
- Run Kubadm init, initialize Kubernetes Cluster
- First phase is pre-flight checks
a. Required permissions on the System
b. Pull Container Images for Control plane (runs as PODs)
c. Validate required System Resource (CPU and Memory)
d. Checks for compatible Container Runtime and is it running (Startup Type: Automatic)
- Creates a Certificate Authority for authentication and encryption
- Creates kubeconfig files for authenticating various components of Kubernetes against API server
- Create Static Pod Manifests for Control Plane Pods
- Kubeadm starts Control plane (i.e API server, Schedular, Etcd and Control Manager) as Pods
- Kubeadm then taints the Master (User Pods will not run on Master), only System Pods will run on Master
- Kubeadm generates Bootstrap token for joining additional Nodes to the Cluster
- Kubeadm then starts Add-on Pods (DNS/Kube-proxy)
Adding Node to the Cluster
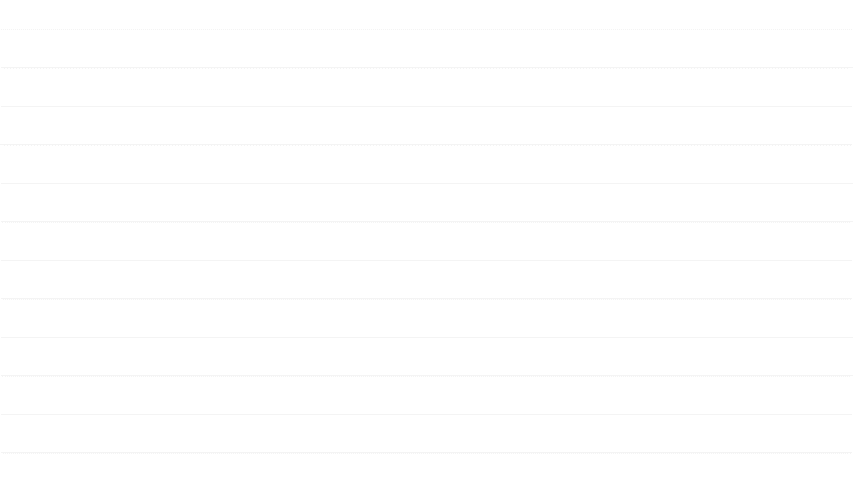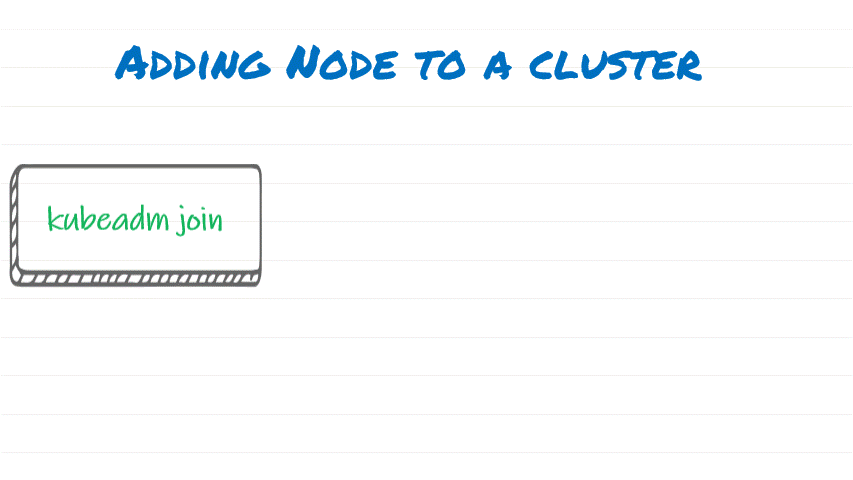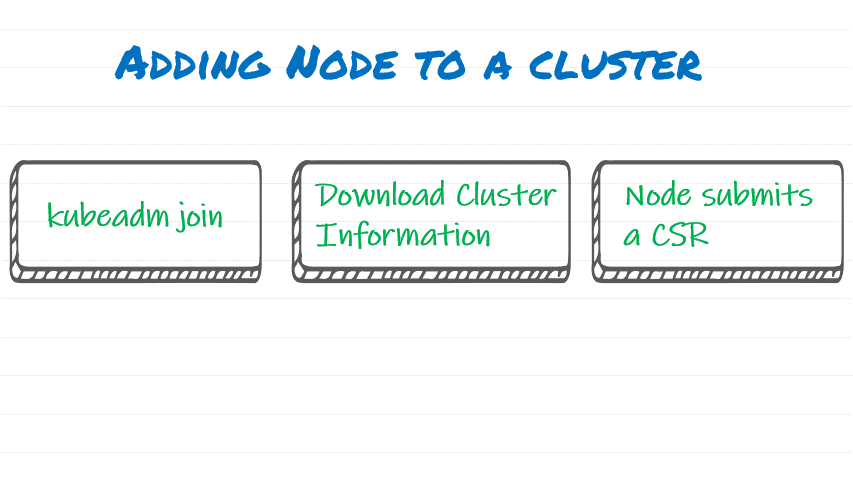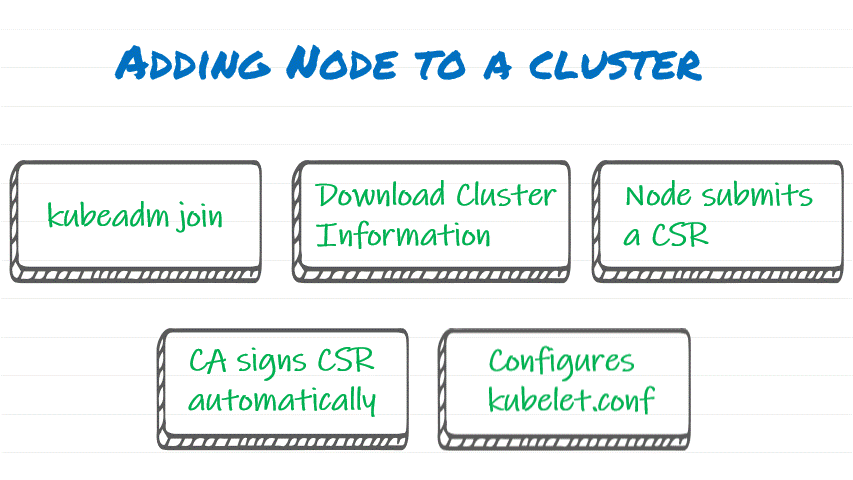
Step by Step process:
- Run Kubeadm join and pass ‘Join Token’ with CA Cert hash
- Node will download Cluster Information
- Node submits CSR request into the API Server to generate a certificate to be used the Kubelet
- CA will automatically sign that CSR, and the Kubeadm is going to download that Certificate and store that on the files system on the Node
- That certificate is going to live in the /var/lib/kubelet.pki
- Kubeadm is then going to generate kubelet.conf file that consist of a pointer to Client Certificate and also the location of API server designated to authenticate this Node. This process is called TLS Bootstrapping